What is a RAT?
RAT: So basically Rat is known as a Remote administrator tool. It Is Used to hack remote A PC without any authentication. There are so many Similar Rat tools Available Online . Rat Allows a Remote attacker to control the infected Computer according to his own wish and Way to carry out many kind of malicious & illegal activity as he has the complete administrator rights of the Remote Computer . Remote administration tool like dark comment is installed on victim’s Computer without the victim’s knowledge.
Basic Functions of RAT are -
⦁ Capture Webcam images
⦁ Turn Firewall on/off
⦁ Simple Pranks by deleting files & turning off computer
⦁ Let's us execute virus in the victim’s PC
⦁ Enables us to download files from victim’s PC
⦁ DDos from victim’s PC
Below are some names of different types of RAT Software’s -
===========================================================
Dark Comet RAT
Black shades RAT
Xtreme RAT
Cybergate RAT
Sub Seven
Pain RAT
JRAT
Net Devil
Apocalypse RAT
Shark RAT
Back Orifice
Bandook RAT
Bifrost
LANfiltrator
Optix Pro
ProRat
So This Were Some Basic Information About The Rat.Let's now move to the our main Topic Tracing The Hacker.
Requirements :
1. TCPView
2. Knowledge about process running in windows
3. Little Knowledge About Rats
4. Brain
First Of All let's Assume that You Are The victim Of A rat. You realized it when you started noticing some unusual activities taking place on your computer. like some of the programs get closed without your permission , Your webcam start automatically, PC shuts downs automatically and other things !.
So while the hacker is connected to your PC, he is in danger too as he can be traced easily. Now we are going to use a tool which can help us to find the attackers IP address, Geographical Location and a lot more information about the attacker.
TCPView: It is program that shows the complete detailed listings of all TCP and UDP endpoints on your system, it including the local, remote addresses and state of TCP connections. As almost all remote hacks are prepared over the Internet, you will be able to use TCPView Which Will Help You To Find If Any Remote PC Is Connected To Your PC. In Simple Language It Allows us to view all the TCP/IP connections on your Computer.
So Download TCP View from the below given link and extract all the files on the Desktop And then Start TCPView.
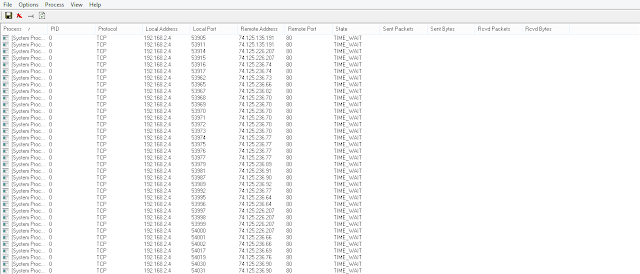
Now as you can see in the screenshot above it displays all of the active TCP/IP connections on your computer. If there is a remote user connected to your computer at this time, then TCPView will show their connection, IP address & other details.
So here I have Infected my own computer with my own RAT. As you can see in the image a Reverse Connection has been Established on the ip 127.0.0.1 which is localhost. Here as an Attacker i am using local host ip address for the reverse connection. But In Your case the attacker will use the static IP address So that he will be Connected to Your PC Permanently. In the image also Check the Port No. 1604 ! Looking Odd ?? Actually there is no Service which runs on the Port No. 1604 For More Info you can Check On Google. So Once you have Found out the attackers IP Address now its time to locate the infected file, where it is placed! . To Locate the Infected RAT file Just Double Click On It and you Can also Kill the Connection now . So Just Right Click On the Unknown Connection and Kill the Task & then you are completely done!. You computer is now disinfected & you also got the IP Address of the attacker.
Here's the screenshot of the Location of the RAT file that you the Victim Installed Our PC.
Later you can do whatever you want to do with the attackers IP Address. Report it to the cyber police or Attack him back & blah blah !!
Be Safe! Keep Hacking !

















0 comments:
Post a Comment